Opened 11 months ago
Last modified 11 months ago
#6810 new defect
[macOS] new place for settings starting with A27 ?
| Reported by: | Langbart | Owned by: | |
|---|---|---|---|
| Priority: | Release Blocker | Milestone: | Alpha 27 |
| Component: | Core engine | Keywords: | |
| Cc: | Patch: |
Description (last modified by )
to reproduce
- download latest release candidate releases.wildfiregames.com/rc
- install it and open it
- make a change in the options, e.g.
FPS Overlayticked on - go to your
user.cfg# typical location cd ~/Library/Application\ Support/0ad
- either nothing is there or only your old stuff
- the new place is very nested
cd ~/Library/Containers/com.wildfiregames.0ad/Data/Library/Application\ Support/0ad
Course of action
- check if this was intended and update this article wiki/GameDataPaths#macOS
Notes
When using my compiled version from source, the location is:
cd ~/Library/Application\ Support/0ad
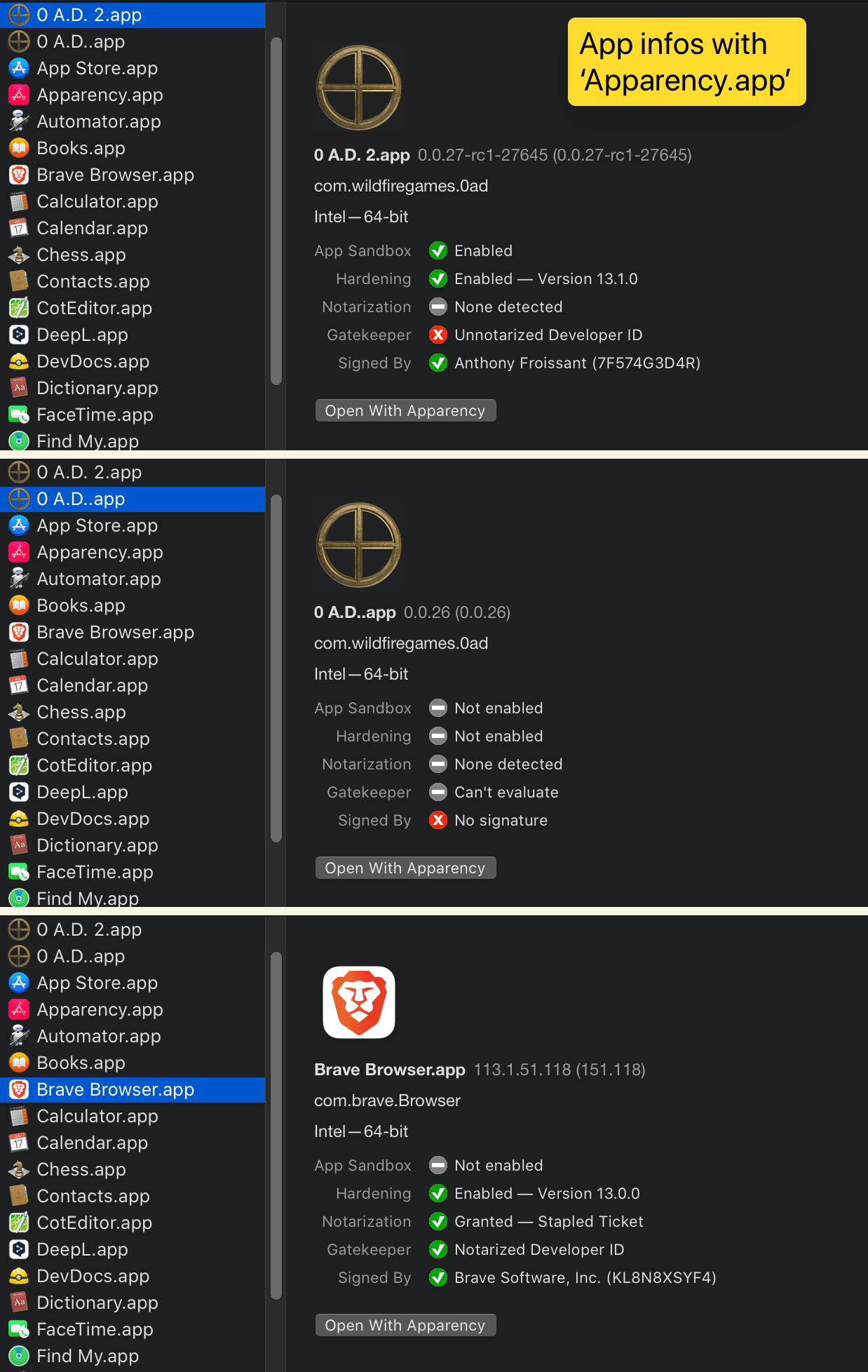
overview of macOS security features
- Image comparing
latest RC,0 A.D. A26andBravewith [Apparency](https://mothersruin.com/software/Apparency/)
Attachments (3)
Change History (12)
follow-up: 3 comment:1 by , 11 months ago
comment:3 by , 11 months ago
Replying to Stan:
I suppose that's because the application is sandboxed to be signed.
Cool, this will solve some issues in the FAQ for macOS.
# see man codesign for used flags codesign --display --verbose=4 /Applications/0\ A.D.\ 2.app/ Executable=/Applications/0 A.D. 2.app/Contents/MacOS/pyrogenesis Identifier=com.wildfiregames.0ad Format=app bundle with Mach-O thin (x86_64) CodeDirectory v=20500 size=629153 flags=0x10000(runtime) hashes=19650+7 location=embedded VersionPlatform=1 VersionMin=658432 VersionSDK=852224 Hash type=sha256 size=32 CandidateCDHash sha256=fcb200bc7824eea5a7169752647a8de3bac4ce53 CandidateCDHashFull sha256=fcb200bc7824eea5a7169752647a8de3bac4ce53216b817056b5bb405cbc501e Hash choices=sha256 CMSDigest=fcb200bc7824eea5a7169752647a8de3bac4ce53216b817056b5bb405cbc501e CMSDigestType=2 Executable Segment base=0 Executable Segment limit=62701568 Executable Segment flags=0x1 Page size=4096 CDHash=fcb200bc7824eea5a7169752647a8de3bac4ce53 Signature size=9053 Authority=Developer ID Application: Anthony Froissant (7F574G3D4R) Authority=Developer ID Certification Authority Authority=Apple Root CA Timestamp=17 May 2023 at 16:01:11 Info.plist entries=15 TeamIdentifier=7F574G3D4R Runtime Version=13.1.0 Sealed Resources version=2 rules=13 files=92 Internal requirements count=1 size=184
Replying to Stan:
Just out of curiosity, did you use the x86 or the m1 version?
0ad-0.0.27-rc1-27645-alpha-x86_x64.dmg
Will there be now two locations for possible macOS config values ?
I have got a couple of other Apps installed, that are also signed, e.g. BraveBrowser and their location remains in ~/Library/Application Support/BraveSoftware.
comment:4 by , 11 months ago
BraveBrowserain't sandboxed, is this required for0 A.D.?
# To display the entitlements of a binary or bundle: codesign --display --entitlements :- /Applications/0\ A.D.\ 2.app/
Executable=/Applications/0 A.D. 2.app/Contents/MacOS/pyrogenesis <?xml version="1.0" encoding="UTF-8"?> <!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd"> <plist version="1.0"> <dict> <key>com.apple.security.app-sandbox</key> <true/> <key>com.apple.security.cs.allow-unsigned-executable-memory</key> <true/> <key>com.apple.security.network.client</key> <true/> <key>com.apple.security.network.server</key> <true/> </dict> </plist>
codesign --display --entitlements :- /Applications/Brave\ Browser.app/
Executable=/Applications/Brave Browser.app/Contents/MacOS/Brave Browser <?xml version="1.0" encoding="UTF-8"?> <!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd"> <plist version="1.0"> <dict> <key>com.apple.application-identifier</key> <string>KL8N8XSYF4.com.brave.Browser</string> <key>com.apple.developer.associated-domains.applinks.read-write</key> <true/> <key>com.apple.developer.networking.vpn.api</key> <array> <string>allow-vpn</string> </array> <key>com.apple.security.device.audio-input</key> <true/> <key>com.apple.security.device.bluetooth</key> <true/> <key>com.apple.security.device.camera</key> <true/> <key>com.apple.security.device.print</key> <true/> <key>com.apple.security.device.usb</key> <true/> <key>com.apple.security.personal-information.location</key> <true/> <key>keychain-access-groups</key> <array> <string>KL8N8XSYF4.com.brave.Browser.devicetrust</string> <string>KL8N8XSYF4.com.brave.Browser.webauthn</string> </array> </dict> </plist>
comment:5 by , 11 months ago
Sandboxing was introduced in 10.7 Lion and is a requirement for all Apple App Store applications. You can also sandbox applications which you distribute outside the App Store, but it is not required. Source: wiki.freepascal.org/Sandboxing_for_macOS
In order to distribute apps thru Mac App Store, developers must turn on App Sandbox entitlement. Source: Using App Sandbox for macOS App
If 0 A.D. shall be in the Mac App Store it needs to be sandboxed, will it be ?
by , 11 months ago
| Attachment: | appstore.png added |
|---|
comment:6 by , 11 months ago
Will there be now two locations for possible macOS config values ?
Yeah I guess so.
I have got a couple of other Apps installed, that are also signed, e.g. BraveBrowser and their location remains in ~/Library/Application Support/BraveSoftware.
I suppose brave cannot be sandboxed for security because it needs more access. You can check the entitlements of an app (understand the list of features it can use) by using the following command
codesign -d --entitlements - --xml /Applications/Whatever.app
I used Warzone as an example => https://github.com/Warzone2100/warzone2100/blob/master/macosx/Resources/Warzone.entitlements
- OpenTTD doesn't seem to have any entitlements https://github.com/orudge/OpenTTD/blob/master/.github/workflows/release.yml
- OpenRA doesn't have sandbox https://github.com/OpenRA/OpenRA/blob/52a916012f262f462f6b5a2af69b38787b10375d/packaging/macos/entitlements.plist
- Godot I couldn't find, but they mention sandboxing
- Supertuxkart doesn't is not signed https://github.com/supertuxkart/stk-code/issues/2534
- Beyond All Reason and all spring games don't work on macos
- Megaglest doesn't seem to be signed https://github.com/MegaGlest/megaglest-source/blob/develop/mk/macos/make-release-archives.sh
- Wesnoth is sandboxed https://github.com/wesnoth/wesnoth/blob/master/projectfiles/Xcode/Resources/Wesnoth.entitlements
- Xonotic is sandboxed https://gitlab.com/rpdev/opentodolist/-/blob/development/app/OpenTodoList.entitlements
If 0 A.D. shall be in the Mac App Store it needs to be sandboxed, will it be ?
I can make the new RC without the flag I suppose. It probably won't be for the next alpha, as it probably will need more time (discussion with SPI is slow) And we have some issues with GPL3 IIRC.
comment:7 by , 11 months ago
| Description: | modified (diff) |
|---|
- add an overview image for macOS enabled security features
by , 11 months ago
| Attachment: | Apparency.png added |
|---|
follow-up: 9 comment:8 by , 11 months ago
Great so it seems you lose the notarization either when copying the app to your application folder, or when downloading it.
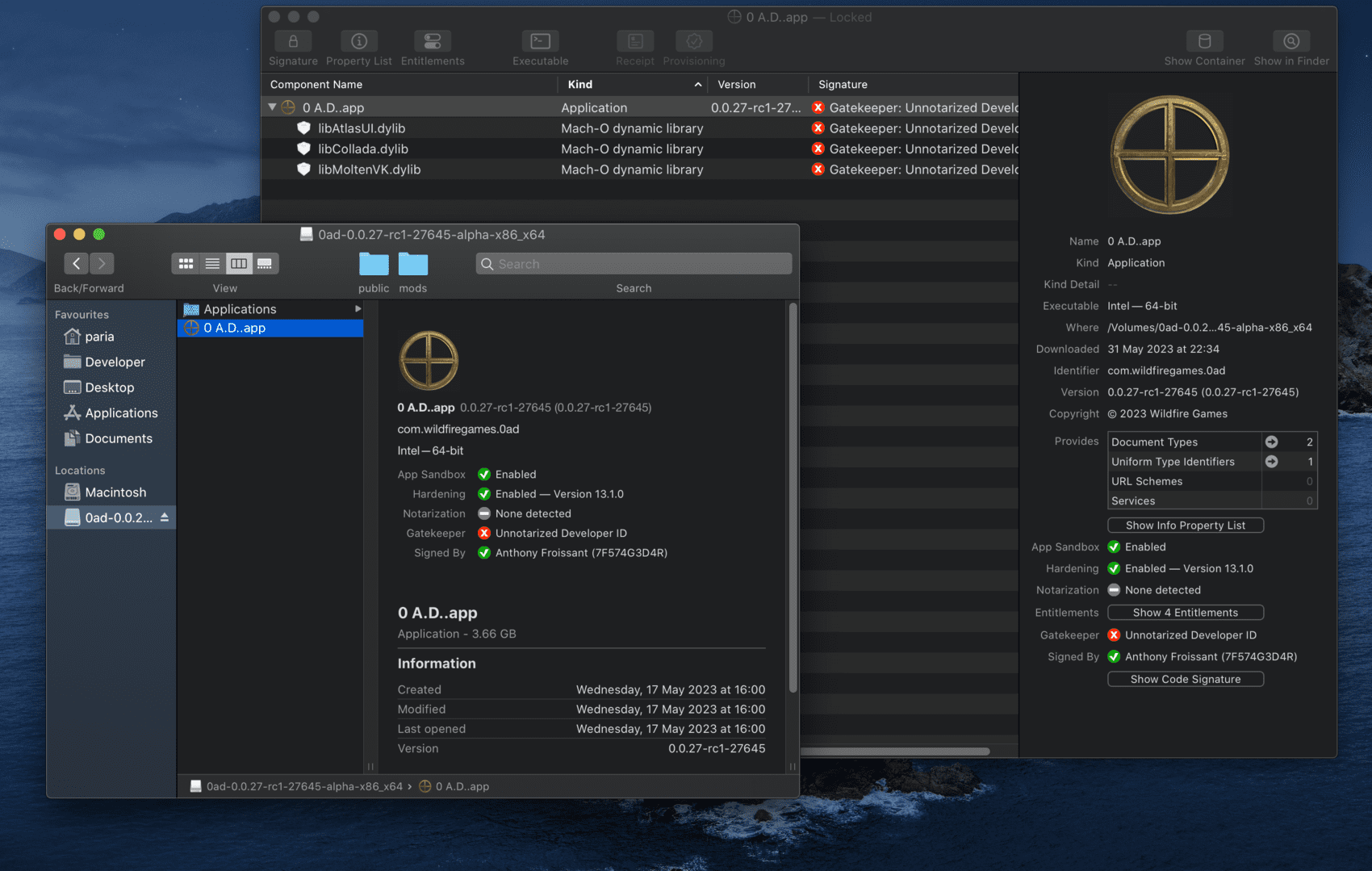
Can you somehow show the one in the DMG?
comment:9 by , 11 months ago
Replying to Stan:
Will there be now two locations for possible macOS config values ?
Yeah I guess so.
If 0 A.D. doesn't go in the mac AppStore, disabling sandboxing should fix this ticket, and no modder will have to update their description with a new location for macOS mods folder.
Replying to Stan:
Can you somehow show the one in the DMG?
This is the screenshot of inside the dmg file.
by , 11 months ago
| Attachment: | inside_dmg.png added |
|---|
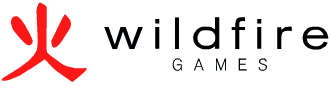

I suppose that's because the application is sandboxed to be signed.
https://developer.apple.com/documentation/bundleresources/entitlements/com_apple_security_app-sandbox
https://apple.stackexchange.com/questions/290310/whats-the-purpose-of-library-containers/290312